Making Sharing Data Smarter, Easier and More Secure
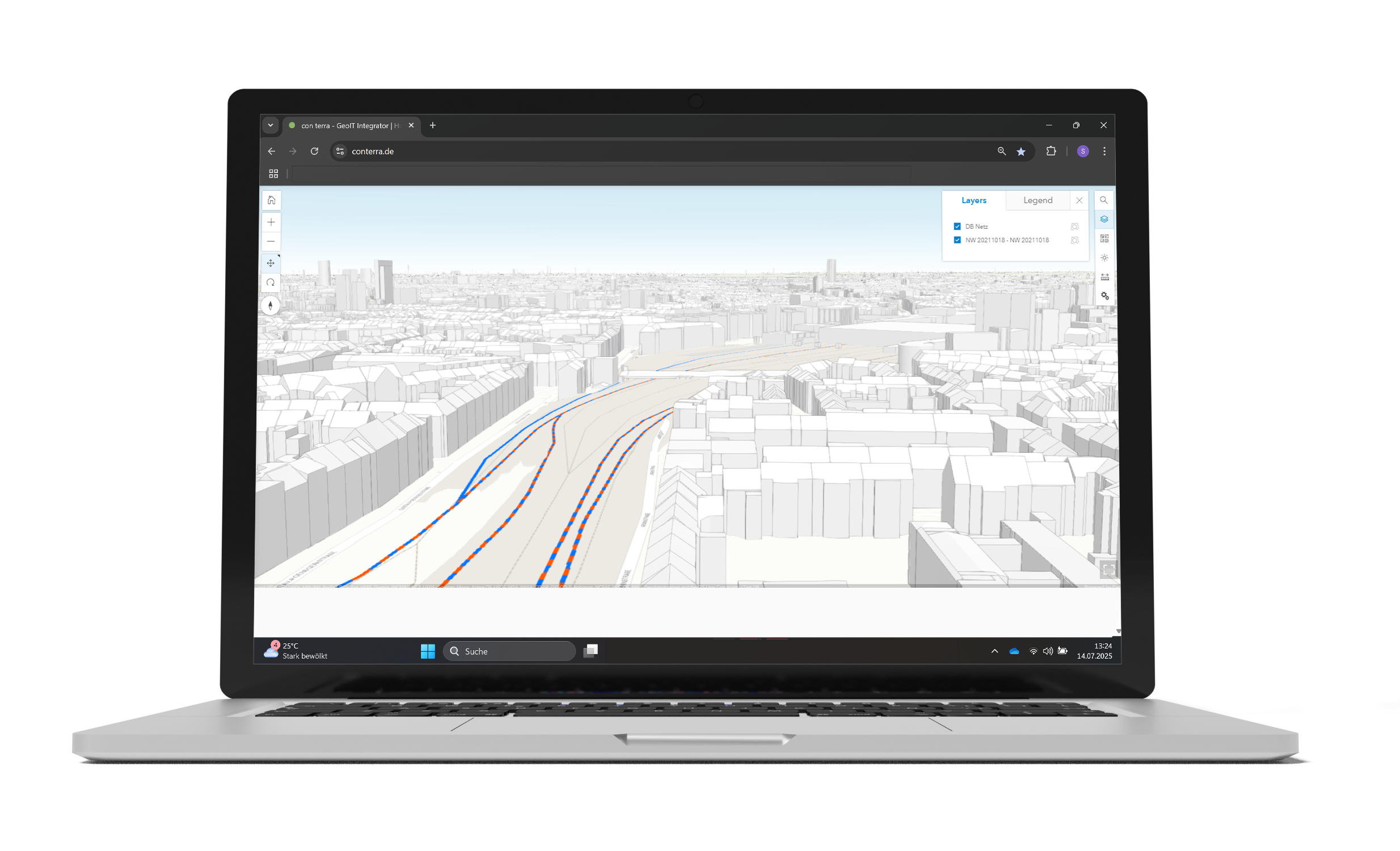
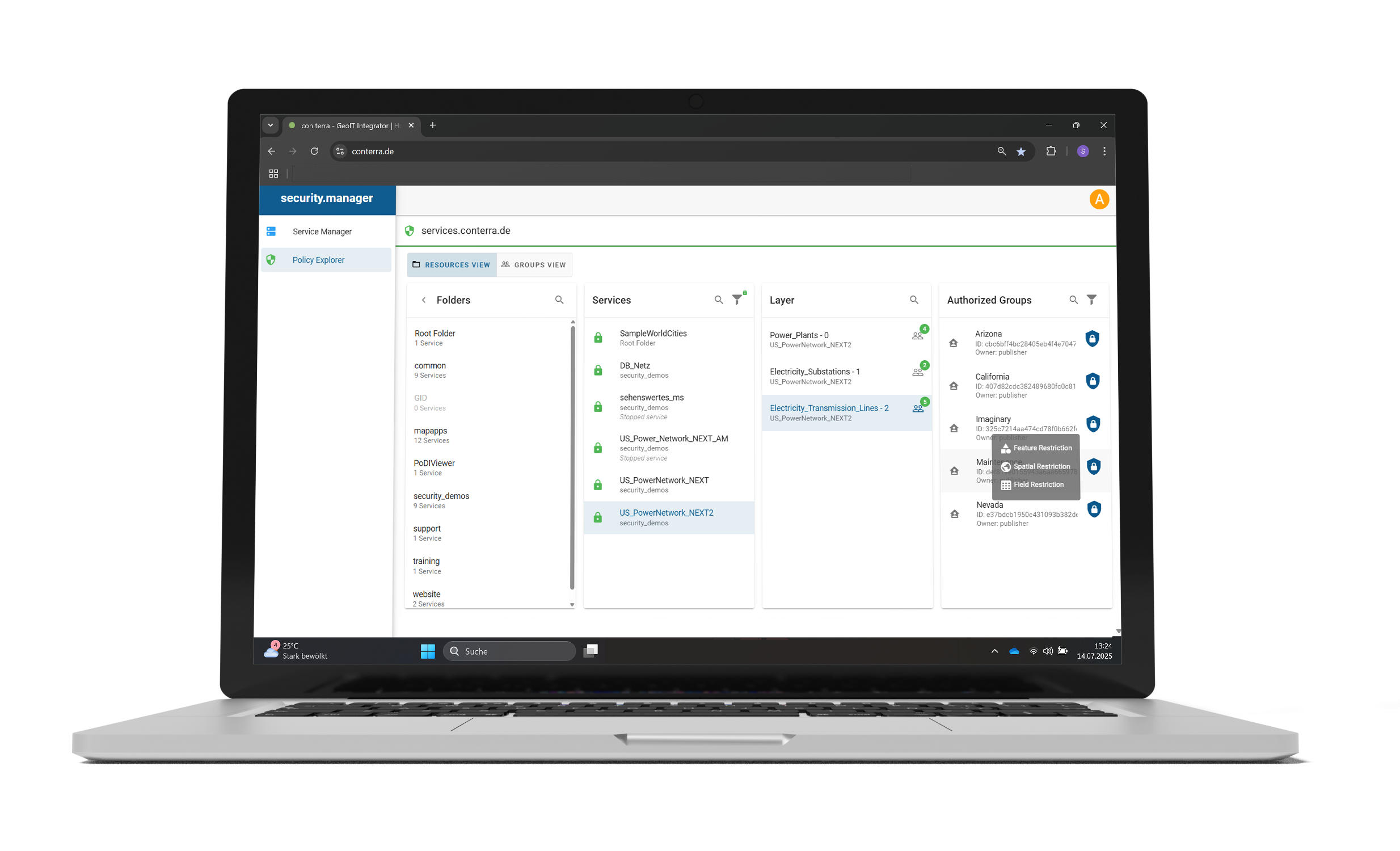
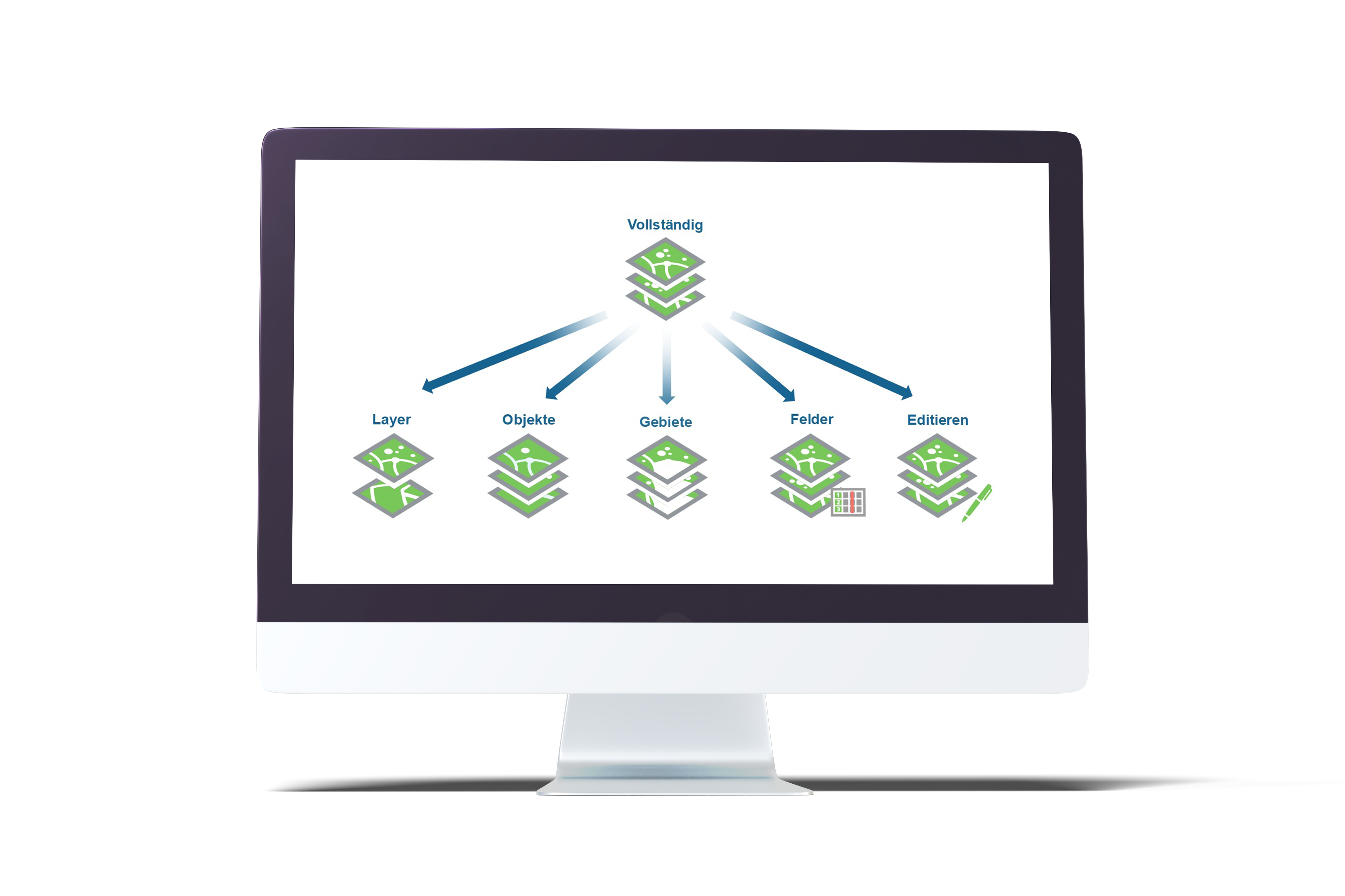
With security.manager, GIS administrators can restrict access to spatial data at a granular level. This allows them to limit the view of layers, objects, attributes and spatial areas, as well as editing rights. This means that all users, whether internal or external, only see the data that has been released for them. security.manager works so efficiently, intelligently, and securely that administrative effort is reduced and data redundancy is minimised.
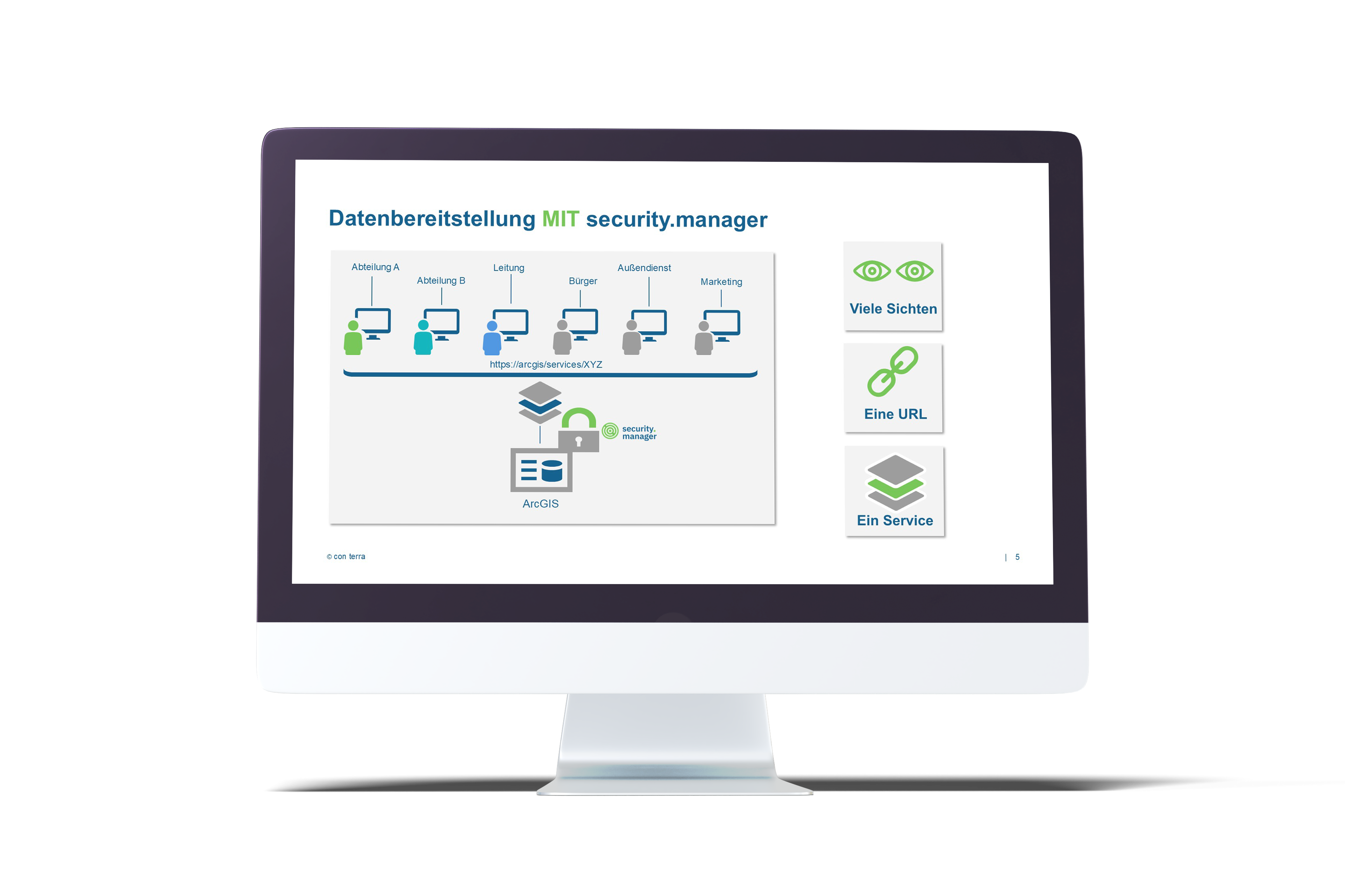
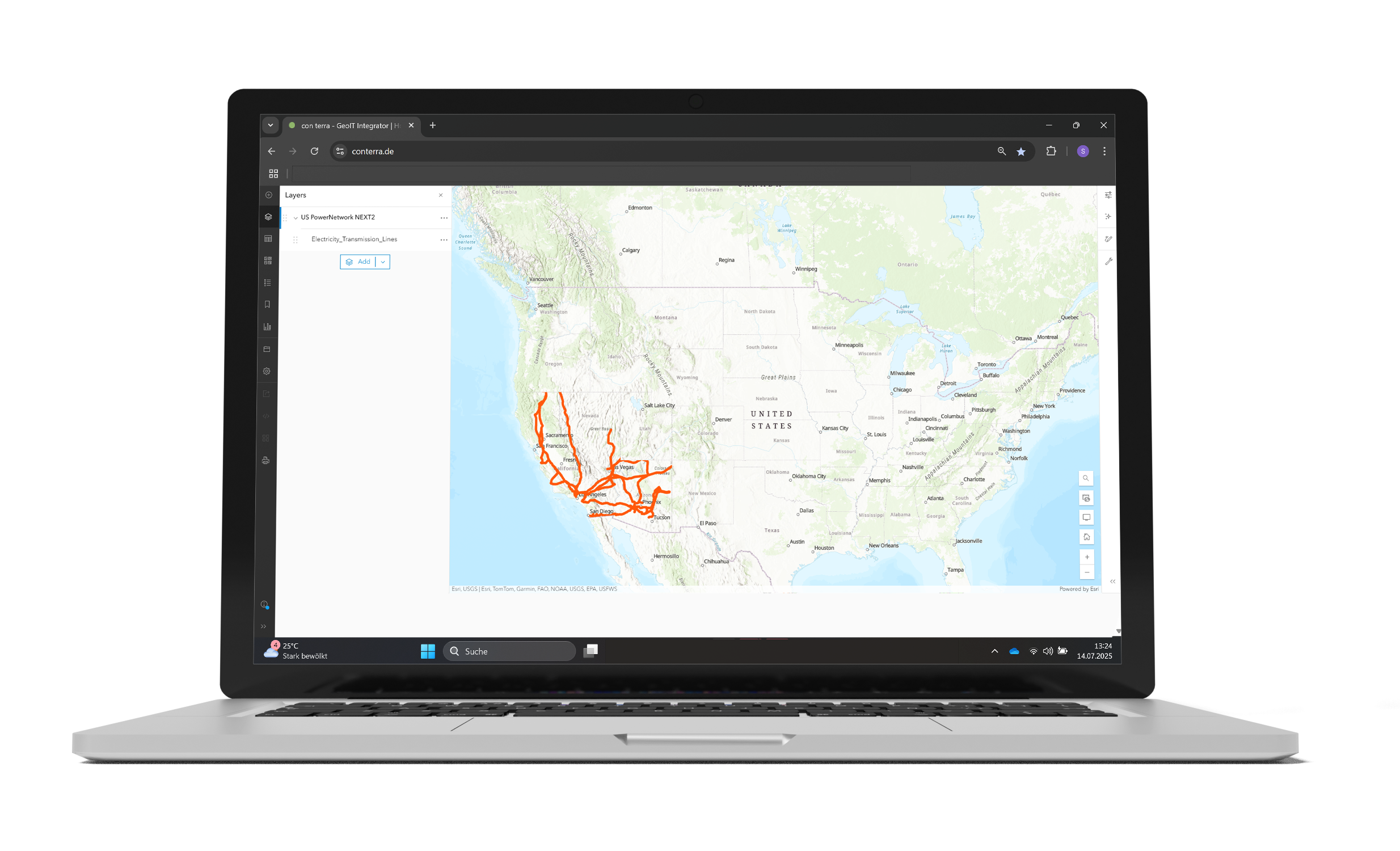
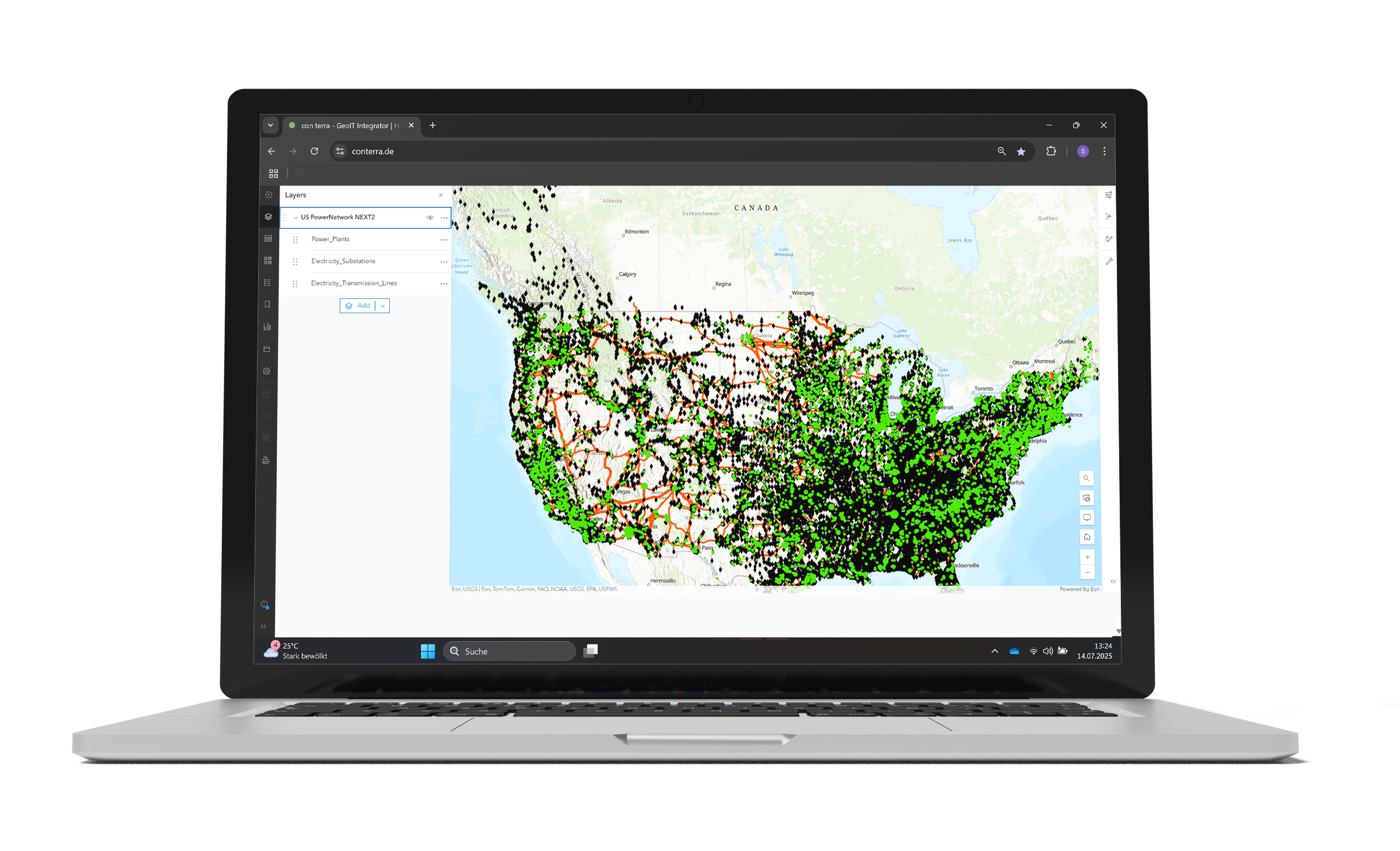
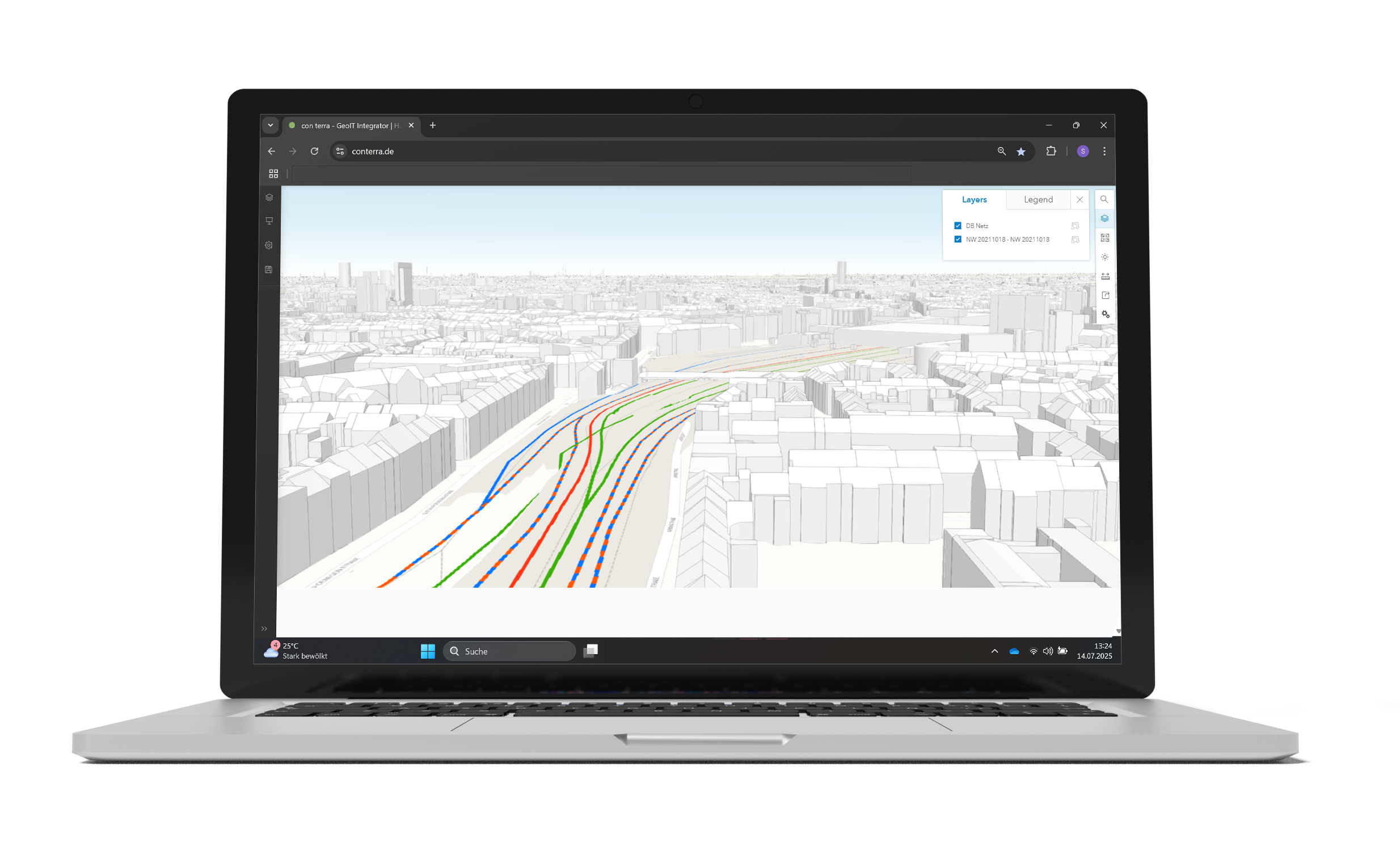
Instead of publishing services redundantly, security.manager filters the spatial data at the source. This means that only one service needs to be published, and all users can access it via the same URL.
security.manager works invisibly in the background: users do not notice that data is being hidden from them. After logging in, each group only sees what it is allowed to see.
security.manager enables the creation of fine-grained permissions. Anything that is not explicitly authorised is automatically prohibited. This reliably prevents unauthorised access to sensitive data.

Without security.manager, we would still keep our geodata in the closet and inaccessible. security.manager opens up complete new possibilities to offer GIS-based web services controlling access precisely for users with different permissions.
- Maps can be published only once and the content filtered individually for different user groups.
- Content can be restricted spatially and at layer, object and attribute level.
- Redundant data storage, map services and apps are eliminated through central filtering.
- Maps, apps and services only need to be published once.
- Access rights can be assigned with a high degree of automation.
- Processes become more efficient and routines are noticeably reduced.
- security.manager integrates transparently.
- Users only see information for which they have explicit authorisation.
- Anything that is not permitted is automatically restricted.

security.manager has made it possible to create one web map and one web app for each department and control how each operates. Without security.manager, we could only achieve fine level control by creating a large number of apps, map services or web maps.
Get to know our editions
security.manager for ArcGIS enables fine-grained access control for ArcGIS services and significantly reduces administrative overhead. Instead of publishing multiple services for different views, a single service can be used, with access controlled down to the layer, feature or attribute level. This allows GIS data to be provided efficiently and securely.

Your benefits at a glance:
Avoidance of redundancy
Individual authorisations within a card
High efficiency through automatability
security.manager for OGC enables the secure sharing of spatial information via OGC services and seamlessly integrates it into modern single sign-on (SSO) infrastructures. Access can be controlled at layer level, via spatial authorisations and for edit operations (WFS-T). This allows OGC services to be provided in a controlled, user-specific and secure manner across the entire organisation.

Your benefits at a glance:
Enterprise SSO for OGC Services
Manufacturer-independent
Fully automatable